Last Updated on January 17, 2025
Identity and Access Management Question CISSP Course: Try this CISSP (Certified Information Systems Security Professional) sample review practice test on Chapter 5: Identity and Access Management for ISC CISSP certification preparation.
Identity and Access Management Question CISSP Course
- Control physical and logical access to assets
- Manage identification and authentication of people, devices, and services
- Federated identity with a third-party service
- Implement and manage authorization mechanisms
- Manage the identity and access provisioning lifecycle
- Implement authentication systems
Identity and Access Management Questions
Q1. Which of the following is best described as an access control model that focuses on subjects and identifies the objects that each subject can access?
- A. An access control list
- B. An implicit denial list
- C. A capability table
- D. A rights management matrix
Q2. Jim’s organization-wide implementation of IDaaS offers broad support for cloud-based applications. Jim’s company does not have internal identity management staff and does not use centralized identity services. Instead, they rely upon Active Directory for AAA services. Which of the following options should Jim recommend to best handle the company’s on-site identity needs?
- A. Integrate on-site systems using OAuth.
- B. Use an on-premises third-party identity service.
- C. Integrate on-site systems using SAML.
- D. Design an internal solution to handle the organization’s unique needs.
Q3. Which of the following is not a weakness in Kerberos?
- A. The KDC is a single point of failure.
- B. Compromise of the KDC would allow attackers to impersonate any user.
- C. Authentication information is not encrypted.
- D. It is susceptible to password guessing.
Q4. Voice pattern recognition is what type of authentication factor?
- A. Something you know
- B. Something you have
C. Something you are - D. Somewhere you are
Q5. If Susan’s organization requires her to log in with her username, a PIN, a password, and a retina scan, how many distinct authentication factor types has she used?
- A. One
- B. Two
- C. Three
- D. Four
Q6. Charles wants to deploy a credential management system (CMS). He wants to keep the keys as secure as possible. Which of the following is the best design option for his CMS
implementation?
- A. Use AES-256 instead of 3DES.
- B. Use long keys.
- C. Use an HSM.
- D. Change passphrases regularly.
Q7. Brian is a researcher at a major university. As part of his research, he logs into a computing cluster hosted at another institution using his own university’s credentials. Once logged in, he is able to access the cluster and use resources based on his role in a research project, as well as using resources and services in his home organization. What has Brian’s home university implemented to make this happen?
- A. Domain stacking
- B. Federated identity management
- C. Domain nesting
- D. Hybrid login
Q8. Place the following steps in the order in which they occur during the Kerberos authentication process.
1. Client/server ticket generated
2. TGT generated
3. Client/TGS key generated
4. User accesses service
5. User provides authentication credentials
- A. 5, 3, 2, 1, 4
- B. 5, 4, 2, 1, 3
- C. 3, 5, 2, 1, 4
- D. 5, 3, 1, 2, 4
Q9. What major issue often results from decentralized access control?
- A. Access outages may occur.
- B. Control is not consistent.
- C. Control is too granular.
- D. Training costs are high.
Q10. Callback to a landline phone number is an example of what type of factor?
- A. Something you know
- B. Somewhere you are
- C. Something you have
- D. Something you are
Q11. Kathleen needs to set up an Active Directory trust to allow authentication with an existing Kerberos K5 domain. What type of trust does she need to create?
- A. A shortcut trust
- B. A forest trust
- C. An external trust
- D. A realm trust
Q12. Which of the following AAA protocols is the most commonly used?
- A. TACACS
- B. TACACS+
- C. XTACACS
- D. Super TACACS
Q13. Which of the following is not a single sign-on implementation?
- A. Kerberos
- B. ADFS
- C. CAS
- D. RADIUS
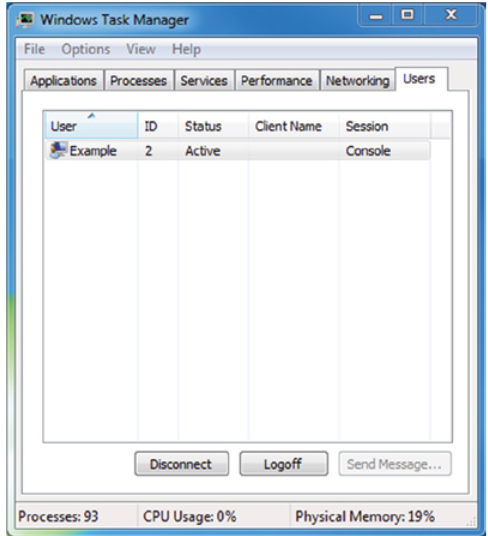
Q14. As shown in the following image, a user on a Windows system is not able to use the Send Message functionality. What access control model best describes this type of limitation?
- A. Least privilege
- B. Need to know
- C. Constrained interface
- D. Separation of duties
Q15. What type of access controls allow the owner of a file to grant other users access to it using an access control list?
- A. Role-based
- B. Nondiscretionary
- C. Rule-based
- D. Discretionary
Q16. Alex’s job requires him to see protected health information (PHI) to ensure proper treatment of patients. His access to their medical records does not provide access to patient addresses or billing information. What access control concept best describes this control?
- A. Separation of duties
- B. Constrained interfaces
- C. Context-dependent control
- D. Need to know
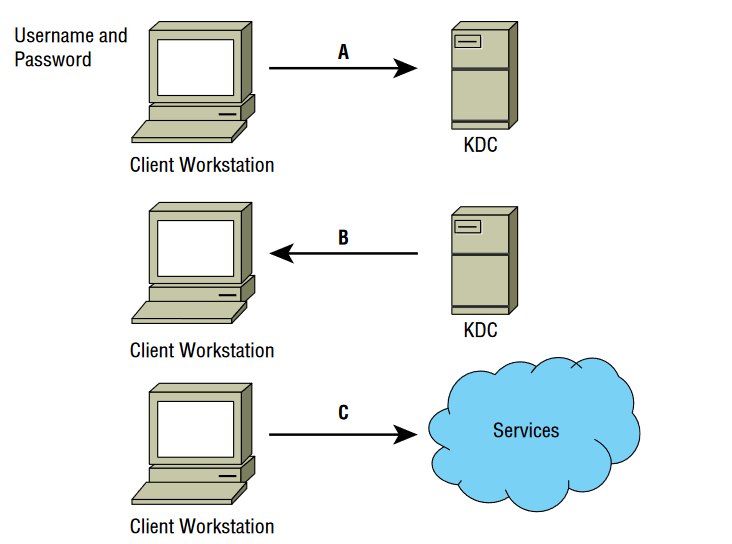
For questions 17–19, please use your knowledge of the Kerberos logon process and refer to the following diagram:
Q17. At point A in the diagram, the client sends the username and password to the KDC. How is the username and password protected?
- A. 3DES encryption
- B. TLS encryption
- C. SSL encryption
- D. AES encryption
Q18. At point B in the diagram, what two important elements does the KDC send to the client after verifying that the username is valid?
- A. An encrypted TGT and a public key
- B. An access ticket and a public key
- C. An encrypted, time-stamped TGT and a symmetric key encrypted with a hash of the user’s password
- D. An encrypted, time-stamped TGT and an access token
Q19. What tasks must the client perform before it can use the TGT?
- A. It must generate a hash of the TGT and decrypt the symmetric key.
- B. It must accept the TGT and decrypt the symmetric key.
- C. It must decrypt the TGT and the symmetric key.
- D. It must send a valid response using the symmetric key to the KDC and must install the TGT.
Q20. Jacob is planning his organization’s biometric authentication system and is considering retina scans. What may concern be raised about retina scans by others in his organization?
- A. Retina scans can reveal information about medical conditions.
- B. Retina scans are painful because they require a puff of air in the user’s eye.
- C. Retina scanners are the most expensive type of biometric device.
- D. Retina scanners have a high false-positive rate and will cause support issues.
See also:
- FREE CISSP Practice Test 2025 Official Study Guide [PDF]
- Security and Risk Management Practice Test
- Asset Security Practice Test
- Security Architecture and Engineering Practice Test
- Communication and Network Security Practice Test
- Identity and Access Management (IAM) Practice Test
- Security Assessment and Testing Practice Test
- Security Operations Practice Test
- Software Development Security Practice Test