Last Updated on January 17, 2025
Security Architecture and Engineering Question CISSP Course: Try this CISSP (Certified Information Systems Security Professional) sample review practice test on Chapter 3: Security Architecture and Engineering for ISC CISSP certification preparation.
This chapter presents the following:
• System architecture
• Trusted computing base and security mechanisms
• Information security software models
• Assurance evaluation criteria and ratings
• Certification and accreditation processes
• Distributed systems security
• Cryptography components and their relationships
• Steganography
• Public key infrastructure (PKI)
• Site and facility design considerations
• Physical security risks, threats, and countermeasures
• Electric power issues and countermeasures
• Fire prevention, detection, and suppression
Security Architecture and Engineering
Q1. Matthew is the security administrator for a consulting firm and must enforce access controls that restrict users’ access based on their previous activity. For example, once a consultant accesses data belonging to Acme Cola, a consulting client, they may no longer access data from Acme’s competitors. What security model best fits Matthew’s needs?
- A. Clark-Wilson
- B. Biba
- C. Bell-LaPadula
- D. Brewer-Nash
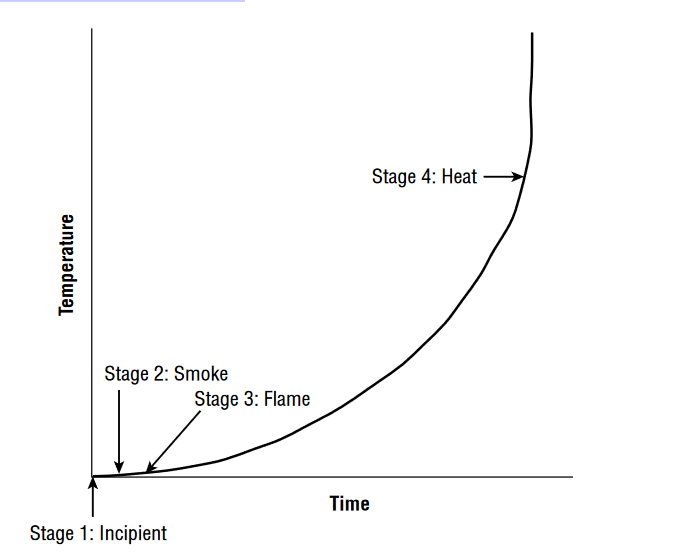
Q2. Referring to the figure shown here, what is the earliest stage of a fire where it is possible to use detection technology to identify it?
- A. Incipient
- B. Smoke
- C. Flame
- D. Heat
Q3. Ralph is designing a physical security infrastructure for a new computing facility that will remain largely unstaffed. He plans to implement motion detectors in the facility but would also like to include a secondary verification control for physical presence. Which one of the following would best meet his needs?
- A. CCTV
- B. IPS
- C. Turnstiles
- D. Faraday cages
Q4. Harry would like to retrieve a lost encryption key from a database that uses m of n control, with m = 4 and n = 8. What is the minimum number of escrow agents required to retrieve the key?
- A. 2
- B. 4
- C. 8
- D. 12
Q5. Fran’s company is considering purchasing a web-based email service from a vendor and eliminating its own email server environment as a cost-saving measure. What type of cloud computing environment is Fran’s company considering?
- A. SaaS
- B. IaaS
- C. CaaS
- D. PaaS
Q6. Bob is a security administrator with the U.S. federal government and wants to choose a digital signature approach that is an approved part of the federal Digital Signature Standard under FIPS 186-4. Which one of the following encryption algorithms is not an acceptable choice for use in digital signatures?
- A. DSA
- B. HAVAL
- C. RSA
- D. ECDSA
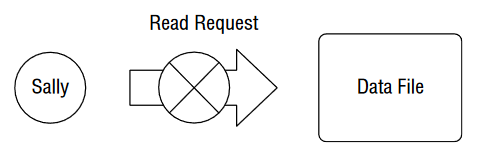
Q7. Harry would like to access a document owned by Sally and stored on a file server. Applying the subject/object model to this scenario, who or what is the subject of the resource request?
- A. Harry
- B. Sally
- C. Server
- D. Document
Q8. Michael is responsible for forensic investigations and is investigating a medium-severity security incident involving a corporate website’s defacement. The web server in question ran on a virtualization platform, and the marketing team would like to get the website up and running as quickly as possible. What would be the most reasonable next step for Michael to take?
- A. Keep the website offline until the investigation is complete.
- B. Take the virtualization platform offline as evidence.
- C. Take a snapshot of the compromised system and use that for the investigation.
- D. Ignore the incident and focus on quickly restoring the website.
- A. Bounds
- B. Input validation
- C. Confinement
- D. TCB
- A. Trust
- B. Credentialing
- C. Verification
- D. Assurance
Q11. What type of security vulnerability are developers most likely to introduce into code when they seek to facilitate their own access, for testing purposes, to software they developed?
- A. Maintenance hook
- B. Cross-site scripting
- C. SQL injection
- D. Buffer overflow
Q12. The figure shows that Sally is blocked from reading the file due to the Biba integrity model. Sally has a Secret security clearance, and the file has a Confidential classification. What principle of the Biba model is being enforced?
- A. Simple Security Property
- B. Simple Integrity Property
- C. *-Security Property
- D. *-Integrity Property
Q13. Tom is responsible for maintaining the security of systems used to control industrial processes located within a power plant. What term is used to describe these systems?
- A. POWER
- B. SCADA
- C. HAVAL
- D. COBOL
Q14. Sonia recently removed an encrypted hard drive from a laptop and moved it to a new device because of a hardware failure. She has difficulty accessing encrypted content on the drive despite knowing the user’s password. What is hardware security feature likely causes this problem?
- A. TCB
- B. TPM
- C. NIACAP
- D. RSA
Q15. Chris wants to verify that a software package he downloaded matches the original version. What hashing tool should he use if he believes that technically sophisticated attackers may have replaced the software package with a backdoor version?
- A. MD5
- B. 3DES
- C. SHA1
- D. SHA 256
For questions Q16–Q19, please refer to the following scenario:
Alice and Bob would like to use an asymmetric cryptosystem to communicate with each other. They are located in different parts of the country but have exchanged encryption keys by using digital certificates signed by a mutually trusted certificate authority.
Q16. If Alice wants to send Bob an encrypted message for confidentiality, what key does she use to encrypt the message?
- A. Alice’s public key
- B. Alice’s private key
- C. Bob’s public key
- D. Bob’s private key
Q17. When Bob receives the encrypted message from Alice, what key does he use to decrypt the message’s plaintext content?
- A. Alice’s public key
- B. Alice’s private key
- C. Bob’s public key
- D. Bob’s private key
Q18. Which one of the following keys would Bob not possess in this scenario?
- A. Alice’s public key
- B. Alice’s private key
- C. Bob’s public key
- D. Bob’s private keY
Q19. Alice would also like to sign the message she sends to Bob digitally. What key should she use to create the digital signature?
- A. Alice’s public key
- B. Alice’s private key
- C. Bob’s public key
- D. Bob’s private key
Q20. What name is given to the random value added to a password in an attempt to defeat rainbow table attacks?
- A. Hash
- B. Salt
- C. Extender
- D. Rebar
See also:
- FREE CISSP Practice Test 2025 Official Study Guide [PDF]
- Security and Risk Management Practice Test
- Asset Security Practice Test
- Security Architecture and Engineering Practice Test
- Communication and Network Security Practice Test
- Identity and Access Management (IAM) Practice Test
- Security Assessment and Testing Practice Test
- Security Operations Practice Test
- Software Development Security Practice Test