Last Updated on January 17, 2025
Security Assessment and Testing Question CISSP Course: Try this CISSP (Certified Information Systems Security Professional) sample review practice test in Chapter 6: Security Assessment and Testing for ISC CISSP certification preparation.
6.1 Design and validate assessment, test, and audit strategies
6.2 Conduct security control testing
6.3 Collect security process data (e.g. technical and administrative)
6.4 Analyze test output and generate report
6.5 Conduct or facilitate security audits
Security Assessment and Testing Question
Q1. During a port scan, Susan discovers a system running services on TCP and UDP 137–139 and TCP 445, as well as TCP 1433. What type of system is she likely to find if she connects to the machine?
- A. A Linux email server
- B. A Windows SQL server
- C. A Linux file server
- D. A Windows workstation
Q2. Which of the following is a method used to design new software tests automatically and to ensure the quality of tests?
- A. Code auditing
- B. Static code analysis
- C. Regression testing
- D. Mutation testing
Q3. During a port scan, Naomi found TCP port 443 open on a system. Which tool is best suited to scanning the service that is most likely running on that port?
- A. zzuf
- B. Nikto
- C. Metasploit
- D. sqlmap
Q4. What message logging standard is commonly used by network devices, Linux and Unix systems, and many other enterprise devices?
- A. Syslog
- B. Netlog
- C. Eventlog
- D. Remote Log Protocol (RLP)
Q5. Alex wants to use an automated tool to fill web application forms to test for format string vulnerabilities. What type of tool should he use?
- A. A black box
- B. A brute-force tool
- C. A fuzzer
- D. A static analysis tool
Q6. Susan needs to scan a system for vulnerabilities, and she wants to use an open source tool to test the system remotely. Which of the following tools will meet her requirements and allow vulnerability scanning?
- A. Nmap
- B. OpenVAS
- C. MBSA
- D. Nessus
Q7. Morgan is implementing a vulnerability management system that uses standards-based components to score and evaluate the vulnerabilities it finds. Which of the following is
most commonly used to provide a severity score for vulnerabilities?
- A. CCE
- B. CVSS
- C. CPE
- D. OVAL
Q8. Jim has been contracted to perform a penetration test of a bank’s primary branch. To make the test as real as possible, he has not been given any information about the bank other than its name and address. What type of penetration test has Jim agreed to perform?
- A. A crystal-box penetration test
- B. A gray-box penetration test
- C. A black-box penetration test
- D. A white-box penetration test
Q9. In a response to a request for proposal, Susan receives an SSAE 18 SOC report. If she wants a report that includes operating effectiveness detail, what should Susan ask for as fol-
low-up and why?
- A. A SOC 2 Type II report, because Type I does not cover operating effectiveness
- B. A SOC 1 Type I report, because SOC 2 does not cover operating effectiveness
- C. A SOC 2 Type I report, because SOC 2 Type II does not cover operating effectiveness
- D. A SOC 3 report, because SOC 1 and SOC 2 reports are outdated
Q10. During a wireless network penetration test, Susan runs aircrack-ng against the network using a password file. What might cause her to fail in her password-cracking efforts?
- A. Using WPA2 encryption
- B. Running WPA2 in Enterprise mode
- C. Using WEP encryption
- D. Running WPA2 in PSK mode
Q11. A zero-day vulnerability is announced for the popular Apache web server in the middle of a workday. In Jacob’s role as an information security analyst, he needs to quickly scan his network to determine what servers are vulnerable to the issue. What is Jacob’s best route to quickly identify vulnerable systems?
- A. Immediately run Nessus against all of the servers to identify which systems are vulnerable.
- B. Review the CVE database to find the vulnerability information and patch information.
- C. Create a custom IDS or IPS signature.
- D. Identify affected versions and check systems for that version number using an automated scanner.
Q12. What type of testing is used to ensure that separately developed software modules properly exchange data?
- A. Fuzzing
- B. Dynamic testing
- C. Interface testing
- D. API checksums
Q13. Selah wants to provide security assessment information to customers who want to use her organization’s cloud services. Which of the following options should she select to ensure that the greatest number of customers are satisfied with the assessment information?
- A. Use an internal audit team to self-assess against internal metrics.
- B. Use a third-party auditor.
- C. Use internal technical staff who know the systems.
- D. Use an internal audit team to self-assess against a common standard like COBIT.
Q14. Yasmine has been asked to consider a breach and attack simulation system. What type ofsystem should she look for?
- A. A ticket and change management system designed to help manage incidents
- B. A system that runs incident response simulations for blue teams to test their skills
- C. A system that combines red and blue team techniques with automation
- D. A security operations and response (SOAR) system
Q15. Monica wants to gather information about security awareness in her organization. What technique is most frequently used to assess security awareness?
- A. Phishing simulators
- B. Gamified applications
- C. Assessment tests
- D. Surveys
Q16. Jim has been contracted to conduct a gray-box penetration test, and his clients have provided him with the following information about their networks so that he can scan them:
Data center: 10.10.10.0/24
Sales: 10.10.11.0/24
Billing: 10.10.12.0/24
Wireless: 192.168.0.0/16
What problem will Jim encounter if he is contracted to conduct a scan from off-site?
- A. The IP ranges are too large to scan efficiently.
- B. The IP addresses provided cannot be scanned.
- C. The IP ranges overlap and will cause scanning issues.
- D. The IP addresses provided are RFC 1918 addresses.
Q17. Mark’s company has been notified that there is a flaw in their web application. The anony- mous individual has notified them that they have two weeks to fix it before the details of the flaw are published along with example exploit code. What industry norm is the individual who contacted Mark’s company violating?
- A. Zero-day reporting
- B. Ethical disclosure
- C. Ethical hacking
- D. The (ISC)2 vulnerability disclosure ethics statement
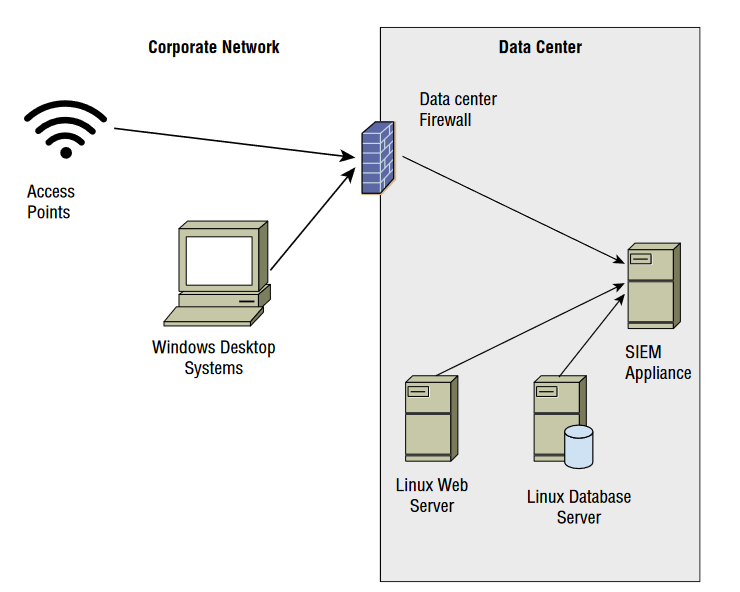
For questions 18–20, please refer to the following scenario:
The company that Jennifer works for has implemented a central logging infrastructure, as shown in the following image. Use this diagram and your knowledge of logging systems to
answer the following questions.
Q18. Jennifer needs to ensure that all Windows systems provide identical logging information to the SIEM. How can she best ensure that all Windows desktops have the same log settings?
- A. Perform periodic configuration audits.
- B. Use Group Policy.
- C. Use Local Policy.
- D. Deploy a Windows syslog client.
Q19. During normal operations, Jennifer’s team uses the SIEM appliance to monitor for exceptions received via syslog. What system shown does not natively have support for syslog events?
- A. Enterprise wireless access points
- B. Windows desktop systems
- C. Linux web servers
- D. Enterprise firewall devices
Q20. What technology should an organization use for each of the devices shown in the diagram to ensure that logs can be time-sequenced across the entire infrastructure?
- A. Syslog
- B. NTP
- C. Logsync
- D. SNAP
See also:
- FREE CISSP Practice Test 2025 Official Study Guide [PDF]
- Security and Risk Management Practice Test
- Asset Security Practice Test
- Security Architecture and Engineering Practice Test
- Communication and Network Security Practice Test
- Identity and Access Management (IAM) Practice Test
- Security Assessment and Testing Practice Test
- Security Operations Practice Test
- Software Development Security Practice Test