Last Updated on January 17, 2025
Software Development Security Question CISSP Course: Try this CISSP (Certified Information Systems Security Professional) sample review practice test in Chapter 8: Software Development Security for ISC CISSP certification preparation.
Software Development Security
- Understand and integrate security into the Software Development Life Cycle (SDLC)
- Identify and apply security controls in software development ecosystems
- Assess the effectiveness of software security
- Assess the security impact of acquired software
- Define and apply secure coding guidelines and standards
Software Development Security Question
Q1. Susan provides a public RESTful API for her organization’s data but wants to limit its use to trusted partners. She intends to use API keys. What other recommendation would you give Susan to limit the potential abuse of the service?
- A. Limit request rates
- B. Force HTTP-only requests
- C. Avoid tokens due to bandwidth constraints
- D. Blacklist HTTP methods such as GET, POST, and PUT
Q2. Darren is conducting a threat hunting exercise and would like to look for botnet indicators of compromise. Which of the following are common ways that attackers leverage botnets? (Select all that apply.)
- A. Mining cryptocurrency
- B. Conducting brute-force attacks
- C. Scanning for vulnerable systems
- D. Conducting man-in-the-middle attacks
Q3. Which one of the following statements is not true about code review?
- A. Code review should be a peer-driven process that includes multiple developers.
- B. Code review may be automated.
- C. Code review occurs during the design phase.
- D. Code reviewers may expect to review several hundred lines of code per hour.
Q4. Kathleen is reviewing the Ruby code shown here. What security technique is this code using?
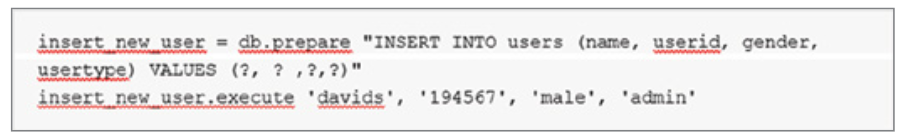
- A. Parameterization
- B. Typecasting
- C. Gem cutting
- D. Stored procedures
Q5. Jessica is reviewing her organization’s change management process and would like to verify that changes to software include acceptance testing. Which process is responsible for achieving this goal?
- A. Request control
- B. Change control
- C. Release control
- D. Configuration control
Q6. Ashley is investigating an attack that compromised an account of one of her users. In the attack, the attacker forced the submission of an authenticated request to a third-party site by exploiting trust relationships in the user’s browser. What type of attack most likely took place?
- A. XSS
- B. CSRF
- C. SQL injection
- D. Session hijacking
Q7. Arnold is creating a new software package and is making use of the OpenSSL library. What term best describes the library he is using?
- A. Open source
- B. COTS
- C. Third-party
- D. Managed
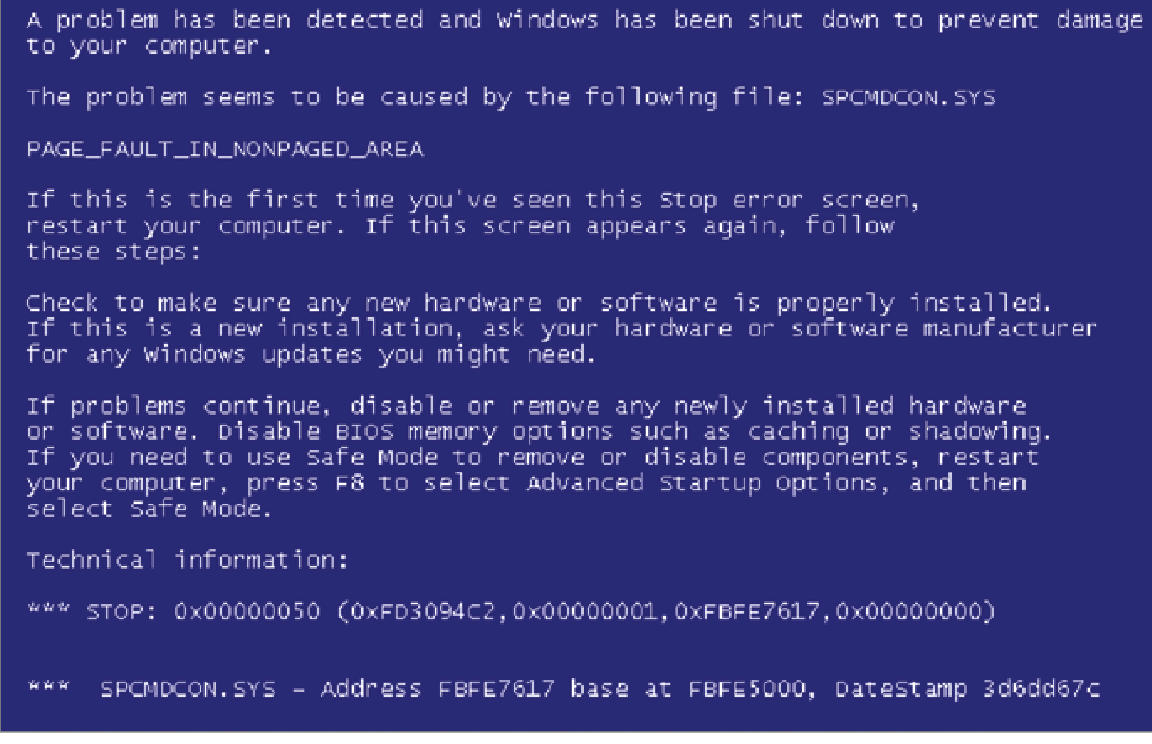
Q8. Jaime is a technical support analyst and is asked to visit a user whose computer is displaying the error message shown here. What state has this computer entered?
- A. Fail open
- B. Irrecoverable error
- C. Memory exhaustion
- D. Fail secure
Q9. Joshua is developing a software threat modeling program for his organization. Which of the following are appropriate goals for the program? (Select all that apply.)
- A. To reduce the number of security-related design flaws
- B. To reduce the number of security-related coding flaws
- C. To reduce the severity of non-security-related flaws
- D. To reduce the number of threat vectors
Q10. In the diagram shown here, which is an example of a method?
Account
Balance: currency = 0
Owner: string
AddFunds(deposit: currency)
RemoveFunds(withdrawal: currency)
- A. Account
- B. Owner
- C. AddFunds
- D. Balance
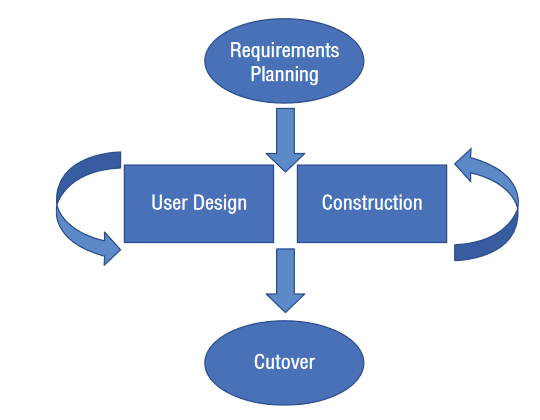
Q11. Wanda is reviewing the application development documentation used by her organization and finds the lifecycle illustration shown here. What application development method is her organization using?
- A. Waterfall
- B. Spiral
- C. Agile
- D. RAD
Q12. Which one of the following testing methodologies typically works without access to source code?
- A. Dynamic testing
- B. Static testing
- C. White-box testing
- D. Code review
Q13. Lucca is analyzing a web application that his organization acquired from a third-party vendor. Lucca determined that the application contains a flaw that causes users who are logged in to be able to take actions they should not be able to in their role. What type of security vulnerability should this be classified as?
- A. Data validation
- B. Session management
- C. Authorization
- D. Error handling
Q14. Bobby is investigating how an authorized database user is gaining access to information outside his normal clearance level. Bobby believes that the user is making use of a type of function that summarizes data. What term describes this type of function?
- A. Inference
- B. Polymorphic
- C. Aggregate
- D. Modular
Q15. Taylor would like to better protect the applications developed by her organization against buffer overflow attacks. Which of the following controls would best provide this protection?
- A. Encryption
- B. Input validation
- C. Firewall
- D. Intrusion prevention system
Q16. Kayla recently completed a thorough risk analysis and mitigation review of the software developed by her team and identified three persistent issues:
1. Cross-site scripting
2. SQL injection
3. Buffer overflows
What is the most significant deficiency in her team’s work identified by these issues?
- A. Lack of API security
- B. Improper error handling
- C. Improper or missing input validation
- D. Source code design issues
For questions 17–20, please refer to the following scenario:
Robert is a consultant who helps organizations create and develop mature software development practices. He prefers to use the Software Capability Maturity Model (SW-CMM) to evaluate the current and future status of organizations using both independent review and self-assessments. He is currently working with two different clients.
Acme Widgets is not very well organized with its software development practices. It does have a dedicated team of developers who do “whatever it takes” to get software out the door, but it does not have any formal processes.
Beta Particles is a company with years of experience developing software using formal, docu- mented software development processes. It uses a standard model for software development but does not have quantitative management of those processes.
Q17. What phase of the SW-CMM should Robert report as the current status of Acme Widgets?
- A. Defined
- B. Repeatable
- C. Initial
- D. Managed
Q18. Robert is working with Acme Widgets on a strategy to advance their software development practices. What SW-CMM stage should be their next target milestone?
- A. Defined
- B. Repeatable
- C. Initial
- D. Managed
Q19. What phase of the SW-CMM should Robert report as the current status of Beta Particles?
- A. Defined
- B. Repeatable
- C. Optimizing
- D. Managed
Q20. Robert is also working with Beta Particles on a strategy to advance their software development practices. What SW-CMM stage should be their next target milestone?
- A. Defined
- B. Repeatable
- C. Optimizing
- D. Managed
See also:
- FREE CISSP Practice Test 2025 Official Study Guide [PDF]
- Security and Risk Management Practice Test
- Asset Security Practice Test
- Security Architecture and Engineering Practice Test
- Communication and Network Security Practice Test
- Identity and Access Management (IAM) Practice Test
- Security Assessment and Testing Practice Test
- Security Operations Practice Test
- Software Development Security Practice Test